This week, a new image hosting website opened. The admin, afraid he might forget his access codes, created a file with credentials on the server. Your goal is to find the file to retrieve his password.
Here is screenshot of this photo gallery.
In html code of it I noticed potential include-attack param “lang”.
<body> <div> <a href = "index.php?lang=eng.php"><img class = "flag" src="includes/flag/eng.png"/></a> <a href = "index.php?lang=fr.php"><img class = "flag" src="includes/flag/fr.png"/></a> </div>
After some fluctuations I found the way to include index.php file itself:
http://gallery.nuitduhack.com/index.php?lang=../../../index.php
Okay. Next step – upload jpeg with malicious code to the server. There are many ways how to do it, but the best of all – brute force (hehe ;) ).
So.. Include malicious jpeg instead of index.php and voila.
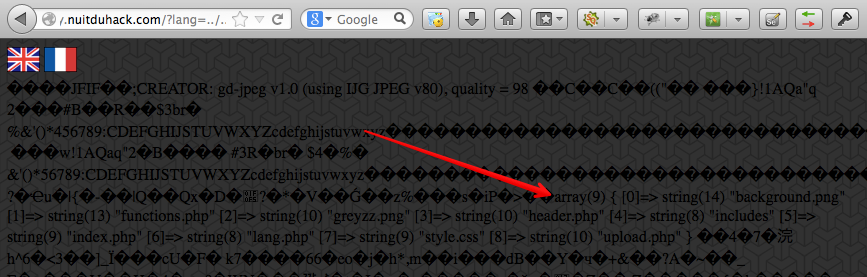
After some search I found file with flag – /includes/X~unsuspicious~X
Okay, it was a little suspicious ..
Here is the flag: WhyAreHemorrhoidsNotCalledAssteroids
Leave a Reply