Are you a good listener? Expect us!
This time you’re the target. :-)
Ok, I started tcpdump on my VPN tunnel interface (all CTF gates are available only through openvpn tunnel) and tooked a waiting position.
18:49:16.639534 IP (tos 0x0, ttl 63, id 6960, offset 0, flags [DF], proto UDP (17), length 64) 10.20.0.1.56581 > 10.20.14.237.53: [udp sum ok] 24723+ MX? dctfu3792.1337.def. (36) 18:49:16.639686 IP (tos 0x0, ttl 64, id 29941, offset 0, flags [none], proto UDP (17), length 92) 10.20.14.237.53 > 10.20.0.1.56581: [udp sum ok] 24723* q: MX? dctfu3792.1337.def. 1/0/0 dctfu3792.1337.def. MX 10.20.14.237. 10 (64)
Looks like someone is trying to use us as DNS server… Okaay, let’s set our ip as mail server (MX) in dnsmasq:
dnsmasq.conf
mx-host=dctfu3792.1337.def,10.20.14.237,100
Then restart dnsmasq, launch nc on smtp (25) port and get back to tcpdump.
Ta-daaaam:
10.20.0.1.36200 > 10.20.14.237.25: Flags [S], cksum 0x2074 (correct), seq 2422406009, win 29200, options [mss 1369,sackOK,TS val 20805670 ecr 0,nop,wscale 7], length 0 18:50:48.022220 IP (tos 0x0, ttl 64, id 1784, offset 0, flags [DF], proto TCP (6), length 64)
Someone is wanted to communicate us via SMTP. Why not? Simulating “SMTP” protocol manually :)
Legend: S – server, C – client.
S: 220 mail.company.tld ESMTP is glad to see you! C: EHLO dns S: 250 domain name should be qualified C: MAIL FROM:<root@dns.def.camp> S: 250 C: RCPT TO:<[email protected].def> S: 250 C: DATA S: 354 Enter mail, end with "." on a line by itself C: Received: by dns (Postfix, from userid 0) id 9961A4D6F; Sat, 3 Oct 2015 17:50:48 +0200 (CEST) Date: Sat, 3 Oct 2015 17:50:48 +0200 From: MISC 500 <misc500@dctf.def.camp> To: [email protected].def Subject: Almost there! Message-ID: <20151003155048.GA338@dns.def.camp> MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="qMm9M+Fa2AknHoGS" Content-Disposition: inline User-Agent: Mutt/1.5.21 (2010-09-15) --qMm9M+Fa2AknHoGS Content-Type: text/plain; charset=us-ascii Content-Disposition: inline Almost... --qMm9M+Fa2AknHoGS Content-Type: application/vnd.tcpdump.pcap Content-Disposition: attachment; filename="ftps.pcap" Content-Transfer-Encoding: base64 1MOyoQIABAAAAAAAAAAAAP//AAABAAAAPyMPVt4oCABKAAAASgAAAAAWPu6kewAWPuiCCggA ...
We received ftpfs.pcap file. This is a traffic dump file. I opened it in wireshark and saw that this is a dump of samba dialogue. I exported SMB object (File->Export Objects -> SMB/SMB2).
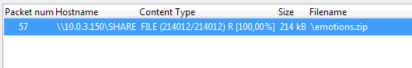
➜ ls
alien.gif
angel.gif
angry.gif
applause.gif
april.gif
atwitsend.gif
battingeyelashes.gif
...
It’s a zipfile with.. what? emotions… aaa.. “Emotional Roller Coaster” :) I opened random gif and saw the following:
<tiff:Model>gAAAAAAAAAEAD9QQAAAABzb2wvVVQFAAPdEA9WdXgLAAEE6AMAAAToAwAAUEsBAh4</tiff:Model>
Looks like it’s base64 encoded data. Then I noticed that these gifs have near modification dates. I tried to fetch all exif data from these gifs in order of their modification:
➜ ls -tr | xargs exiftool | grep 'Camera Model Name' | awk '{print $5}' | base64 -D >b.tmp && file b.tmp b.tmp: Zip archive data, at least v1.0 to extract
➜ unzip b.tmp Archive: b.tmp creating: sol/ extracting: sol/flag inflating: junk inflating: junk (copy) inflating: junk (3rd copy) inflating: junk (4th copy) inflating: junk (5th copy) inflating: junk (6th copy) inflating: junk (7th copy) inflating: junk (8th copy) inflating: junk (9th copy) inflating: junk (10th copy) inflating: junk (11th copy) inflating: junk (12th copy) inflating: junk (another copy)
➜ cat sol/flag DCTF{e4045481e906132b24c173c5ee52cd1e}
Gotcha :)
Flag: DCTF{e4045481e906132b24c173c5ee52cd1e}.
Leave a Reply