We were given a blank page.
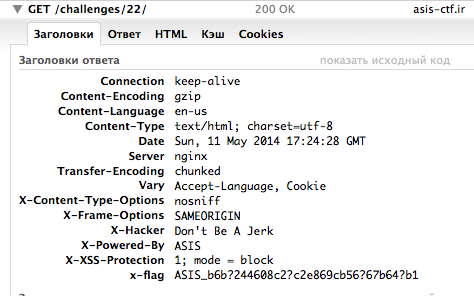
But if we look at http headers, we can see that we have masked flag in them.
All that we need – find masked characters of flag.
 I noticed that in source of any page in this CTF we have js, which calculate sha256(sha256(flag)). And if it matches, sends flag to server.
I noticed that in source of any page in this CTF we have js, which calculate sha256(sha256(flag)). And if it matches, sends flag to server.
So we can brute our flag more quickly.
Here is a according snippet:
$('#flag_submission').submit(function(e){ e.preventDefault(); var shaObj = new jsSHA(document.forms["flag_submission"]["id_flag"].value, "TEXT"); var hash = shaObj.getHash("SHA-256", "HEX"); var shaObj2 = new jsSHA(hash, "TEXT"); var hash2 = shaObj2.getHash("SHA-256", "HEX"); if (document.forms["flag_submission"]["check"].value !== hash2) { ...
Here is script which does this job.
#!/usr/bin/env python import hashlib import sys def run(src): alpha = "0123456789abcdef" pos = src.find('?') if pos == -1: if hashlib.sha256(hashlib.sha256(src).hexdigest()).hexdigest() == "2b127c77074e44b6e74074b1eb8d32dfe27fe78e6a05e302baed68e2cc643ca1": print "Flag: %s" % src sys.exit(0) return for i in xrange(0, alpha.__len__()): cur = src[:pos] + alpha[i] + src[pos + 1:] run(cur) src = "ASIS_b6b?244608c2?c2e869cb56?67b64?b1" run(src)
Leave a Reply